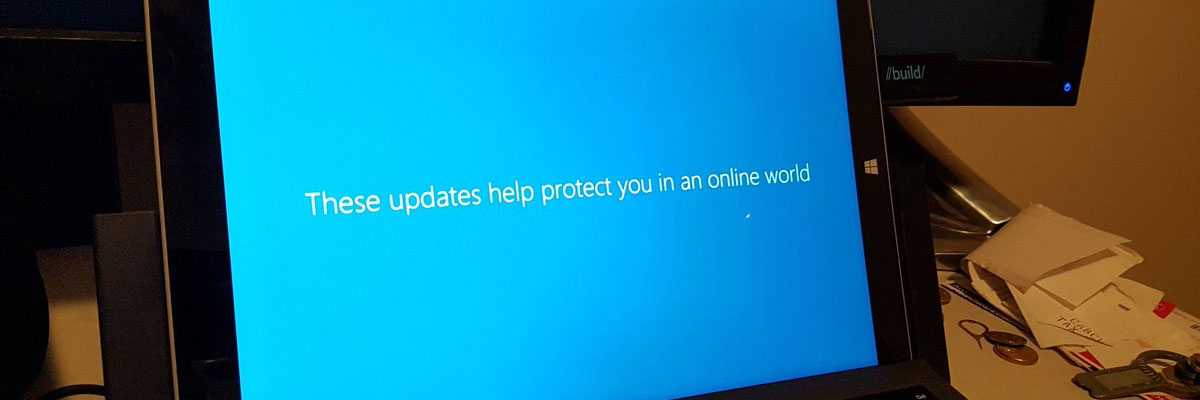
Have you been getting spam mail that looks like this recently?
I know [password redacted] one of your password. Lets get directly to the purpose. You may not know me and you are most likely thinking why you’re getting this e mail? No one has compensated me to check about you.
Well, I installed a software on the xxx vids (sex sites) web-site and you know what, you visited this web site to experience fun (you know what I mean) [no, I don’t actually]. While you were watching video clips, your internet browser started functioning as a Remote control Desktop that has a key logger [if this was anywhere remotely close to true, the open source movement is a complete failure] which provided me with accessibility to your display screen as well as web cam [uh huh. I guess this guy works for the NSA?]. after that, my software collected all your contacts from your Messenger, FB, as well as email [funny, I don’t use Facebook and surely he could at least name specifically the messenger programs I use. Like a cold reading from a psychic, generic terms may fool some victims]. And then I created a double-screen video. First part displays the video you were viewing (you have a good taste lol . . .) [I don’t browse porn either, so I’m curious what YouTube video I’m supposed to be so ashamed of watching], and second part displays the view of your web camera, yeah it is you [Cool, I’m more interested in the program he’s using to see through the piece of electrical tape covering my webcam].
You got not one but two solutions. Shall we check out each one of these possibilities in details:
1st solution is to dismiss this e mail. In this instance, I am going to send your very own video clip to each one of your personal contacts and thus imagine regarding the humiliation yo u will see [I was so excited choosing this solution — I couldn’t wait to see what said webcam footage looked like through the electrical tape!]. Do not forget in case you are in a relationship [“in case I was in a relationship” — for someone that claims to have access to e-mails and social media accounts, you’d think he’d be a little more certain about my relationship status?], just how this will affect?
Other solution is to give me $1000. Lets call it a donation. Consequently, I will quickly eliminate your video recording [Anyone that actually pays this almost deserves to part with their money — if a hacker did the unethical breaching of a system and then went on to extortion, what are the chances he’ll suddenly be honest and “eliminate your video recording” upon payment?]. You can go on with your way of life like this never took place and you will not hear back again from me. [For most victims that receive this e-mail one time, it becomes somewhat believable. Except people have been receiving dozens of this type of extortion e-mail with various amounts and different source e-mail and BitCoin addresses. Who falls for this crap?]
You will make the payment by Bitcoin (if you do not know this, search “how to buy bitcoin” in Google).
BTC Address to send to: [redacted, no accidental “donations” to them please]
[CASE SENSITIVE so copy & paste it]Should you are looking at going to the law enforcement officials, surely, this mail can not be traced back to me [well, BitCoin transactions do leave an electronic paper trail, but I digress]. I have taken care of my moves. I am also not looking to charge you a whole lot, I would like to be paid for. [yes, for all the hard work and contributions you’ve made to society, clearly]
You have one day in order to make the payment. I’ve a special pixel within this message, and at this moment I know that you have read this email message [ah, the dreaded “special pixel”]. If I do not get the BitCoins, I will, no doubt send your video recording to all of your contacts including close relatives, co-workers, and many others [still waiting, we would all like to have a laugh quite honestly]. However, if I receive the payment, I’ll destroy the video immediately. If you really want evidence, reply Yea & I will send out your video to your 9 contacts. This is the non:negotiable offer, that being said don’t waste mine time and yours by replying to this message. [wait, can I reply “Yea” or not? Which one is it? Make up your mind!]
Well, Mr. Aaron Smith, user of Yahoo! Japan e-mail, it’s been a few weeks and perhaps dozens of identical threats and me and my friends are still waiting for the damning video. We’re growing impatient, and if we don’t get said video within two days expect the police to soon be at your door.
The other option is to give us all $1000. Let’s call it a donation. Consequently, your failures in life and lame script kiddie efforts will be forgiven. I mean, how difficult is it to download a widely-accessible database file with leaked account information and passwords (let’s face it, these script kiddies never do the real hacking but rely on mass data leaks someone else accomplished) and spamming their BitCoin addresses with an illogical backstory?
In any case, there are some lessons to be learned by anyone that has been receiving such e-mail lately. Some of the strategies I invoke to ensure that no further damage can be done by careless websites not securing their database or properly encrypting confidential user information:
- Don’t ever use the same password for multiple sites. The exception in this case would be sites that are trivial in nature: accounts that you don’t care if they get hacked. Ask yourself this question when registering: if I publicized my username and password to the entire world for this particular website, would I care if everyone could access that account and do whatever they please? Furthermore, would I care if everyone could also access accounts from other sites that use the same password? If you don’t care, you can use the same password and login information for expediency.
- Otherwise, for websites you do care about because they store sensitive information such as credit cards, addresses, contacts, etc. or play a part in your online identity (forums, messenger apps, e-mail) use a unique username and e-mail upon registration. It is helpful to have an e-mail domain where you can specify anything in front of the “@” symbol and have it arrive to your inbox, but even if you don’t own an e-mail domain and use a third party like @live.com or @protonmail.com, etc. you can still use the trick of adding “+[x]” to provide unique e-mail addresses when registering on different websites. For example, if your email is johnsmith@protonmail.com, you can register with an e-mail like “johnsmith+fakebook-com@protonmail.com”. You will still receive any e-mail sent to “johnsmith+fakebook-com@protonmail.com” in your johnsmith@protonmail.com inbox. If you start receiving spam mail from random sources, you can quickly identify the site with loose security standards by taking a look at the recipient e-mail address (e.g. if it is addressed to johnsmith+fakebook-com, we know fakebook.com had a leak or is misusing your e-mail). Furthermore, you will no longer be low hanging fruit by always having different username/e-mail/password combinations for multiple sites.
- When using unique passwords, it can become difficult to memorize each one, but you can make this task easier by employing a system of writing your passwords down (either on a physical piece of paper, a password-protected spreadsheet, or in an e-mail to yourself) in an encrypted manner. Sort of like how some sites ask you questions like “what is the make of your first car?” or “what is your mother’s maiden name?”, you can ask yourself similar questions, but have a unique way of extracting a strong password from that answer. For example, say your first car was a 2013 Lamborghini Countach, and one of your personal encryption methods was to simply use every other letter in the make and model and sandwiching it with a relevant year (i.e. your password would become “20Lmogiionah03”), all you need to write down on your password reminder sheet is “Your first car”. Now you only have to memorize the system, which you can employ with several other passwords, allowing you to have many unique and strong passwords without having to memorize much. This also prevents you from becoming low hanging fruit. No one wants to be like John Podesta with useless passwords such as “passw0rd”.
Remember that when large database leaks occur such as the Yahoo! Mail hack or Equifax hack, always assume the worst. Everything you put out there on the Internet is pretty much for everyone to see (at some point in time). When it comes time to do firefighting when one of your accounts gets exposed, you’ll want to make sure the fire doesn’t spread so rapidly by having the same username/e-mail/password combination spread over multiple sites.
* * *
If you found this article helpful, “you got not one but two solutions: 1st solution is to dismiss this [post]. Other solution is to give me $1000″.
Just kidding. But do consider the advice about unique e-mails, usernames and passwords, leave a comment, share the article with friends and family you care about, and if you are going the donation route, visit the Donate page or follow some of my other work.